Controlled Unclassified Information (CUI) Scoping Guidance
The scoping tree shown below is updated for the October 2024 CMMC 2.0 Scoping Guide criteria. You can click on the image to download a PDF of this scoping guide.
Unified Scoping Guide (USG)
The Unified Scoping Guide (USG) is a free resource that is intended to help organizations define the scope of the sensitive data where it is stored, transmitted and/or processed. This guide will refer to both sensitive and regulated data as “sensitive data” to simplify the concept this document is focused on. This model categorizes system components according to several factors:
- Whether sensitive data is being stored, processed or transmitted;
- The functionality that the system component provides (e.g. access control, logging, antimalware, etc.); and
- The connectivity between the system and the sensitive data environment
The USG can be used to help companies define what is in scope to comply with NIST SP 800-171 and appropriately prepare for a CMMC assessment, since a significant step towards becoming NIST SP 800-171 compliant and being able to pass a CMMC assessment is understanding the scope of the Controlled Unclassified Information (CUI)environment. The USG includes the DoD's CMMC 2.0 Level 2 Scoping Guidance that addresses CUI scoping considerations, but is also useful to address s a broader category of sensitive and regulated data. Why is this important? For many organizations, protecting CUI is just one of many data types that it is legally obligated to protect.
The Unified Scoping Guide (USG) is intended to help organizations define the scope of the sensitive data where it is stored, transmitted and/or processed. This guide will refer to both sensitive and regulated data as “sensitive data” to simplify the concept this document is focused on. This approach is applicable to the following sensitive data types:
|
|
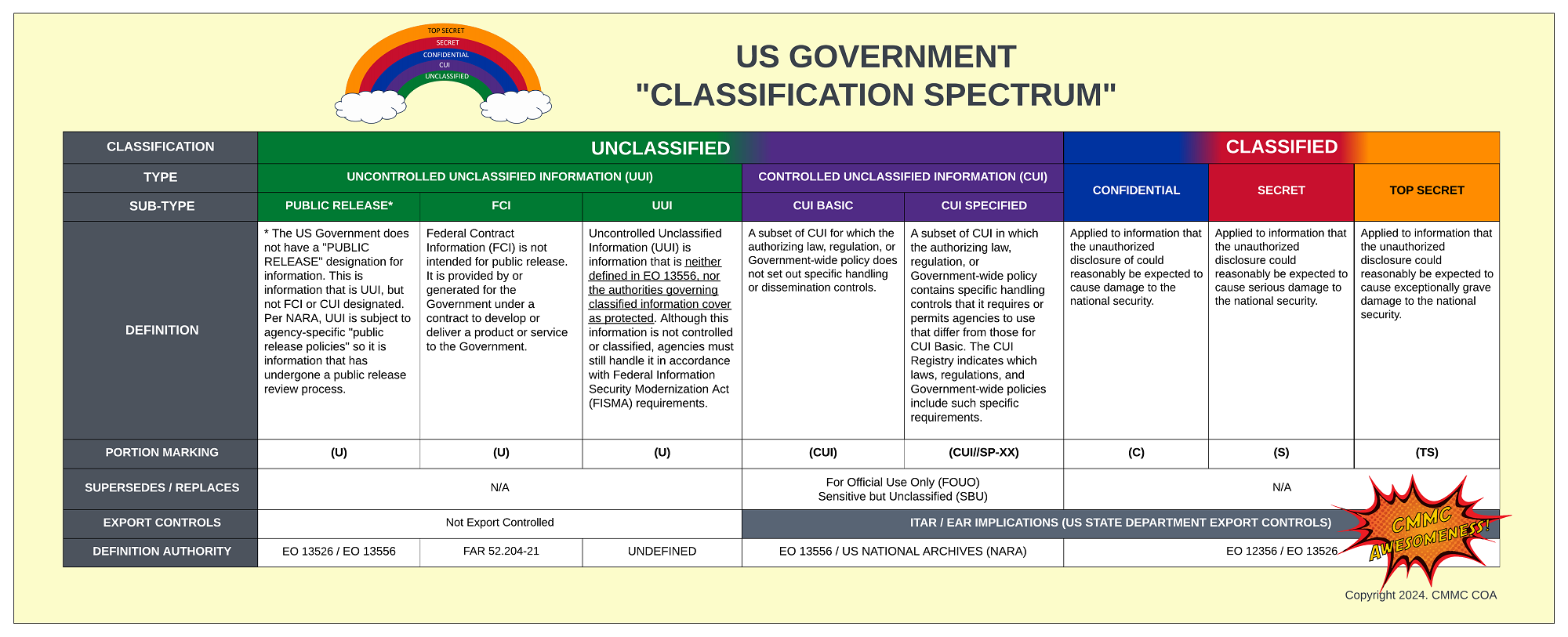
Understanding The Difference Between "Classified" and "Unclassified" Information
It is important to start out by level-setting the understanding that NIST 800-171 and CMMC focus entirely on UNCLASSIFIED data. Where there is common confusion is that UNCLASSIFIED data is broken down into two types and several sub-types, as shown below.
Take A Zone-Based Approach To Implementing Data-Centric Security
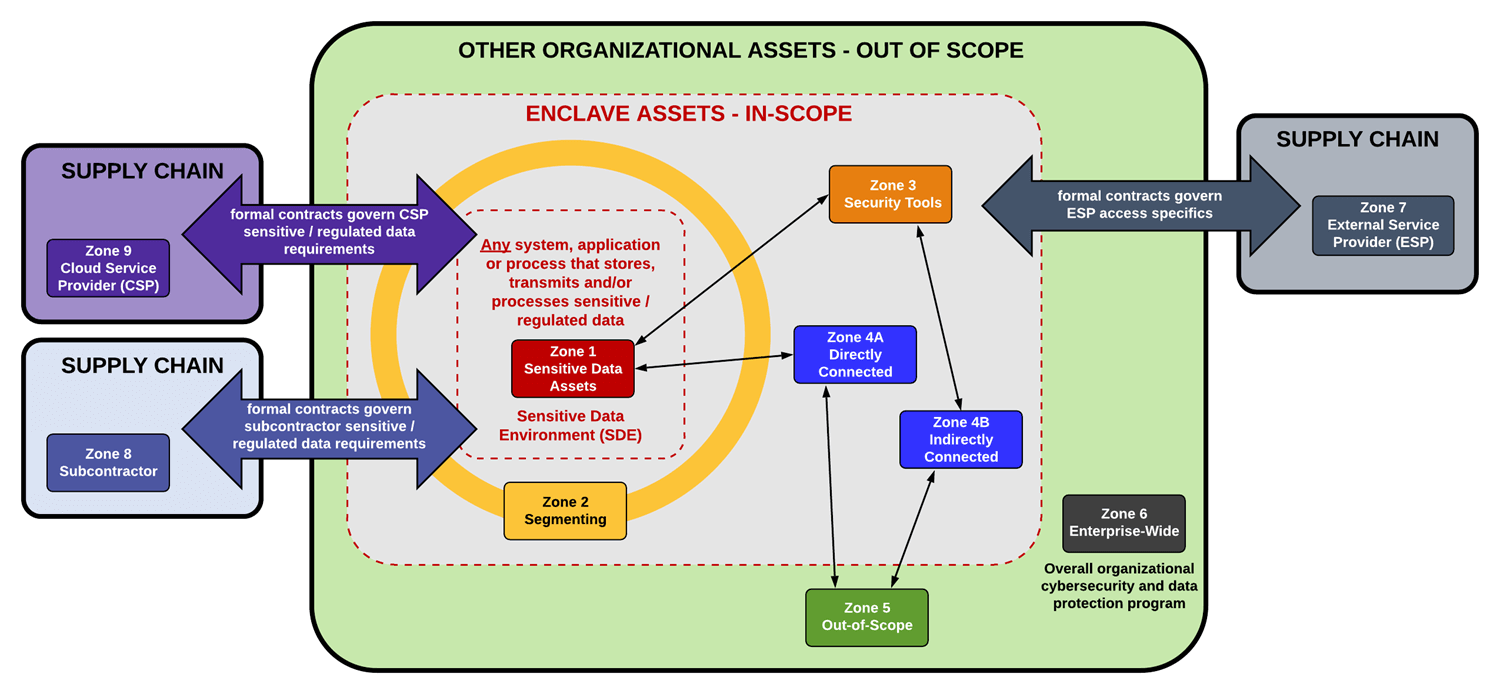
The Unified Scoping Guide (USG) takes a zone-based approach to scoping, where there are eight (8) zones for sensitive/regulated data compliance purpose.
- Sensitive Data Assets: The first zone contains systems, services and applications that directly store, transmit and/or process sensitive data.
- Segmenting: The second zone contains “segmenting systems” that provide access (e.g., firewall, hypervisors, etc.).
- Security Tools: The third zone contains “security tools” that directly impact the integrity of category 1 and 2 assets (e.g., Active Directory, centralized antimalware, vulnerability scanners, IPS/IDS, etc.).
- Connected. The fourth zone contains connected systems. These are systems, embedded technologies, applications or services that have some direct or indirect connection into the sensitive data environment. Systems, embedded technologies, applications and services that may impact the security of (for example, name resolution or web redirection servers) the sensitive data environment are always in scope. Essentially, it something can impact the security of sensitive data, it is in scope.
- Out-of-Scope. The fifth zone contains out-of-scope systems that are completely isolated from the sensitive data systems.
- Enterprise-Wide. The sixth zone addresses the organization’s overall corporate security program (cyber and physical).
- External Service Provider. The seventh zone addresses supply-chain security with the “flow down” of contractual requirements to External Service Providers (ESPs) that can directly or indirectly influence the sensitive data environment. ESPs are third-party organizations that provide services to the organizations.
- Subcontractors. The eighth zone addresses subcontractors, which are third-party organizations that are party to the actual execution of the contract where the subcontractor may create, access, receive, store and/or transmit regulated data (sensitive data).
- Cloud Service Providers. The nineth zone addresses CSPs, which are a specialized form of ESP. An ESP is a CSP when it offers “cloud computing services” that enable ubiquitous, convenient, on-demand network access to a shared pool of configurable computing resources (e.g., networks, servers, storage, applications, and services) that can be rapidly provisioned and released with minimal management effort or service provider interaction