Oct 22nd 2024

CMMC Center of Awesomeness (CMMC COA)
What happens when a group of cybersecurity practitioners has a dark sense of humor and too much time on their hands? Well... this is it! This is not affiliated with the DoD or CyberAB. This is an independent project to help those dealing with NIST 800-171 & Cybersecurity Maturity Model Certification (CMMC) compliance issues. We completely understand that CMMC is a dumpster fire and we support any effort to fix CMMC and transform it into a viable, scalable Supply Chain Risk Management (SCRM) solution for the US Defense Industrial Base (DIB).
On a serious note, we've seen a "money grab" as CMMC has become its own cottage industry and we wanted to do something to help those in the DIB by providing a starting point to understand what possible technology options exist. There are free tools, references and a list of consultants so there are a lot of options at your disposal.
This information is "use at your own risk" so you are fully-expected to do your own due diligence and due care when selecting any product or service, otherwise you are an idiot and you seriously should not be supporting the DIB in the first place! Seriously.
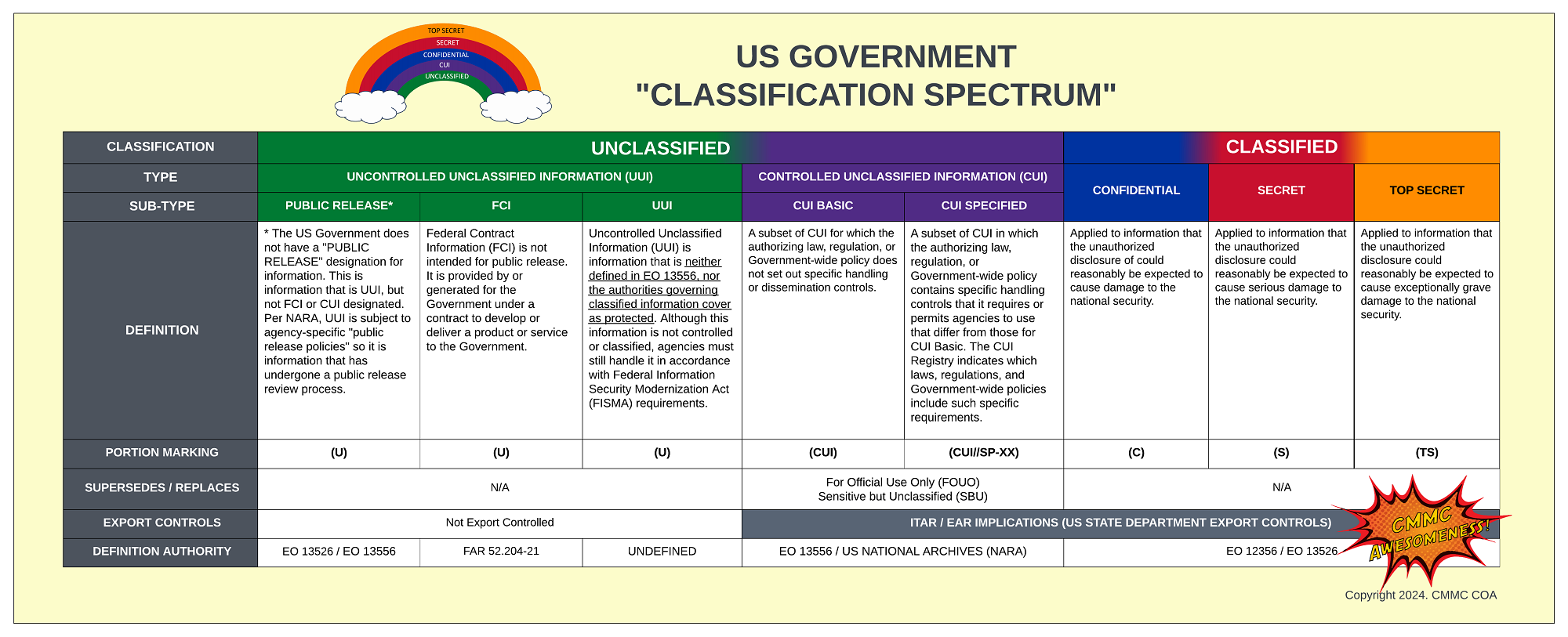
The CMMC Center of Awesomeness (CMMC-COA) project is a volunteer effort. We received a lot of input and recommendations from cybersecurity practitioners who are very experienced in NIST SP 800-171 and CMMC. These valuable insights are what made this project useful, since what might work for PCI DSS, HIPAA, SOC 2, etc. does not necessarily mean it will work for CMMC, based on the data-centric nature of protecting regulated data, which is Federal Contract Information (FCI) for CMMC Level 1 and Controlled Unclassified Information (CUI) & FCI for CMMC Levels 2-3.
The CMMC-COA is an attempt to help the DIB attain CMMC awesomeness! This is a free resource to help those in the DIB get pointed in the right direction. The idea behind the way information is presented is that the size of an Organization Seeking Assessment (OSA) / Organization Seeking Certification (OSC) best determines the budget/staffing/complexity more than any other single aspect. That is why the technology solutions are proposed according to the following Bureau of Labor Statstics (BLS) firm size guidelines:
- Micro-Small Business (<10 staff) BLS Firm Size Classes 1-2
- Small Business (10-49 staff) BLS Firm Size Classes 3-4
- Medium Business (50-249 staff) BLS Firm Size Classes 5-6
- Large Business (250-999 staff) BLS Firm Size Classes 7-8
- Enterprise (> 1,000 staff) BLS Firm Size Class 9
Cybersecurity Maturity Model Certification (CMMC)
Do yourself a favor by making a cup of coffee and reading through the DoD's official Frequently Asked Questions (FAQ) for the recent 32 CFR CMMC Program Rule. This is content that everyone should be familiar with to help avoid assumptions. You can download the FAQ for free directly from the DoD: https://dodcio.defense.gov/Portals/0/Documents/CMMC/CMMC-FAQs.pdf
It is going to be a waiting game to see how the DoD and CMMC-AB roll out "CMMC 3.0" with the release of NIST 800-171 R3, given the significant difference in the volume of controls that exist between R2 and R3 of NIST 800-171. Regardless of it being a waiting game, it is imperative that you take this time to educate yourself on the basics. First, start with the DoD's website about CMMC. The following graphics are meant to help break down some of the basic concepts about the remaining 3 levels of CMMC 2.0 that will exist, which essentially are made up of pre-existing standards:
- Level 1 has 17 controls that are sourced directly from the 15 basic cybersecurity controls in FAR 52.204-21.
- Level 2 has 110 controls that are sourced directly from NIST SP 800-171. However, do not forget the 61 Non-Federal Organization (NFO) controls in Appendix E of NIST SP 800-171.
- Level 3 has all the tantalizing goodness of Level 2, but adds controls from NIST SP 800-172. This will end up being a subset of the 35 controls found in NIST SP 800-172.


CMMC Awesomeness Spreadsheet
At the heart of what we've done is create the "CMMC Awesomeness Spreadsheet" that you can download as an Excel file.
There is no endorsement of any kind for products or services listed on this website. It should not be needed, but we have to call out that it is entirely your responsibility to conduct appropriate due diligence and due care in selecting and engaging a product or service for implementation against CMMC practices and processes within your organization. Your responsibility, not ours! Yours!
To wrap your head around CMMC, it is worth your time to watch the video below. This is "A Banquet of Consequences: The Story of CUI, DFARS & CMMC" by Jacob Horne. This is an excellent, in-depth look into the origins of CMMC that proves the point that CMMC was not "sprung upon the DIB" without warning... a nearly two decades-long glacier that "suddenly appeared" out of nowhere.
"Good Security" Follows The CIAS Quadrant Model
Just to make it painfully clear, we feel it is important to point out that NIST SP 800-171 and CMMC only focus on the CONFIDENTIALITY and INTEGRITY of regulated data (specifically CUI and FCI). This does not equate to "good security" for the overall organization, just minimal requirements for an OSC to contractually fulfill its obligation to protect its client's data (e.g., DoD's FCI and CUI data).
The four pillars of a modern cybersecurity program are Confidentiality, Integrity, Availability and Safety and that should be the guiding concept that you use when evaluating and selecting any technology solutions for your organization: