CMMC Kill Chain: Managing Your Critical Resources & Acquisition Path (CRAP)
The concept is straightforward - if you apply a prioritized, phased approach towards CMMC-related pre-assessment activities, it is possible to avoid rework by addressing dependencies earlier in the process. The bottom line is this model breaks down CMMC / NIST 800-171 compliance into major & minor steps, which can then be translated into a project plan. The end result is a viable approach for anyone to use in order to create a prioritized project plan for CMMC / NIST 800-171 pre-assessment activities.
The premise of the Kill Chain is to build a viable project plan from the perspective of a prioritized listing of tasks in order to successfully prepare for and pass a CMMC / NIST 800-171 assessment. Errors or misguided adventures with people, processes and technology earlier in CMMC / NIST 800-171 control implementation activities will have cascading effects, so the Kill Chain is meant to provide a model for prioritizing CMMC / NIST 800-171-related pre-assessment activities.
There are currently two (2) versions of the Kill Chain:
- CMMC 2.0 / NIST 800-171 R2
- NIST 800-171 R3
Kill Chain Version - CMMC 2.0 / NIST 800-171 R2
The CMMC 2.0 & NIST 800-171 R2 version of the CMMC Kill Chain introduces the theory of constraints as it applies to your Critical Resources & Acquisition Path (CRAP). Yes. The CMMC Kill Chain will help you figure out and manage your CRAP.
Here is information on the 23 phases of the CMMC Kill Chain (these correspond to the picture diagram):
- Define What CUI Is For Your Specific Business Case. This should be self-explanatory and is based on your contract(s).
- Establish The Scope of The CMMC Assessment Boundary. This has four subcomponent steps: (1) Create a Data Flow Diagram (DFD) that shows how CUI flows from the DoD all the way down to subcontractors; (2) Create a detailed asset inventory for all systems, applications and services for both in-scope and out-of-scope assets; (3) Create a detailed network diagram that includes where CUI is stored, transmitted and/or processed; and (4) Inventory Third-Party Service Providers (TSP) to determine TSP access to CUI and/or in-scope systems, applications and/or services.
- Document The Environment. This has two subcomponent steps: (1) Start populating the System Security Plan (SSP); and (2) Create a Plan of Action & Milestone (POA&M) to track and remediate deficiencies.
- Define The Network Architecture. This involves implementing a network architecture that ensures it is built on secure engineering principles and enclaves to protect sensitive information (e.g., FCI/CUI). POA&M deficiencies & document procedures.
- Plan, Identify Gaps & Prioritize Resources. This has six subcomponent steps: (1) Define applicable statutory, regulatory and contractual obligations (including DFARS, FAR, NIST 800-171 and CMMC); (2) Perform a gap assessment from applicable statutory, regulatory and contractual obligations; (3) Develop & implement policies and standards to address applicable statutory, regulatory and contractual obligations; (4) Identify the necessary People, Processes & Technology (PPT) that are necessary and appropriately sized; (5) Develop & implement a resource plan (e.g., business plan, budget, road map, etc.) to meet compliance obligations; and (6) Prioritize objectives from the resource plan for PPT requirements. POA&M any deficiencies from this phase.
- Develop Procedures. This has two subcomponent steps: (1) Develop & implement procedures to implement policies & standards; and (2) Define processes to securely handle CUI. POA&M any deficiencies from this phase.
- Risk Management. Develop & implement a Risk Management Program (RMP) to identify, assess and remediate risk. POA&M deficiencies & document procedures.
- Change Control. Develop & implement change control processes, including a Change Control Board (CCB). POA&M deficiencies & document procedures.
- Incident Response. Develop & implement incident response capabilities to detect, respond and recover from incidents. POA&M deficiencies & document procedures.
- Situational Awareness. Develop & implement situational awareness capabilities through log collection and analysis (e.g., SIEM). POA&M deficiencies & document procedures.
- System Hardening. Identify, build & implement secure baseline configurations (e.g., hardening standards) for all technology platforms. POA&M deficiencies & document procedures.
- Centralized Management. Build & implement Group Policy Objects (GPOs) for Microsoft Active Directory (AD). POA&M deficiencies & document procedures.
- Identity & Access Management. Develop & implement Identity & Access Management (IAM) to address "least privilege" and Role-Based Access Control (RBAC). POA&M deficiencies & document procedures.
- Maintenance. Develop & implement proactive maintenance practices. POA&M deficiencies & document procedures.
- Attack Surface Management / Vulnerability Management. Develop & implement Attack Surface Management (ASM) practices. POA&M deficiencies & document procedures.
- Asset Management. Develop & implement technology asset management practices. POA&M deficiencies & document procedures.
- Personnel Security. Work with Human Resources (HR) to ensure personnel security requirements are integrated into HR operations. POA&M deficiencies & document procedures.
- Network Security. Develop & implement network security practices. POA&M deficiencies & document procedures.
- Business Continuity. Develop & implement business continuity capabilities. POA&M deficiencies & document procedures.
- Cryptography. Develop & implement cryptographic key management and data encryption capabilities. POA&M deficiencies & document procedures.
- Physical Security. Develop & implement physical security practices. POA&M deficiencies & document procedures.
- Security Awareness Training. Build and maintain a security-minded workforce through training & awareness. POA&M deficiencies & document procedures.
- Internal Audit. Build and maintain an "internal audit" or Information Assurance (IA) capability to govern controls. POA&M deficiencies & document procedures.
Background On The Logic Used In This Model
Here is a quick explanation on some of the reasoning used for this model:
- You can't legitimately assess changes, vulnerabilities, threats, etc. without first having a handle on risk management and a defined risk threshold. Risk management is the key building block that other practices rely upon.
- Once you have solid risk management practices, change control is the second most important phase to address, since that is needed to legitimately alter other practices and you need to be able to document your changes and track open issues in a POA&M (e.g., evidence of due care).
- From there, the assumption is that you will discover issues so incident response capability needs to exist (note - DFARS incident reporting requirements already apply if you currently store, process and/or transmit CUI as part of a DoD contract).
- Event logging/SIEM is next and needs to exist before secure configurations, since logs need to get sent somewhere. You need to have this logging infrastructure in place before you get into secure configurations.
- Secure configurations and centralized management (e.g., GPOs) almost go hand-in-hand, but before you can centrally manage configurations, they need to be defined and standardized.
- Next, identity and access management needs to be locked down to ensure aspects of least privilege and RBAC are implemented. The reason IAM comes after secure configurations is due to troubleshooting - if you have "gold standard" secure builds to work from, it is easier to then assign permissions/RBAC that will work with those builds. The alternative is your new configs break your IAM/RBAC, which is bad. Avoid that.
- You realistically can’t do vulnerability management without first having solid maintenance capabilities, so maintenance needs to be formalized with change control integrations. Maintenance needs to be tied into change management, which has a risk management component to it.
- The concept of vulnerability management is broad and is best summed up by the term “attack surface management” where you are doing what you can to minimize the ways an adversary can attack. This relies on maintenance practices and change management being in place and operating.
- From there, the remaining phases are relatively subjective - it really is. However, the “internal audit” function realistically needs to come last where control validation testing assesses how well controls are implemented. This can help serve as a pre-audit function.
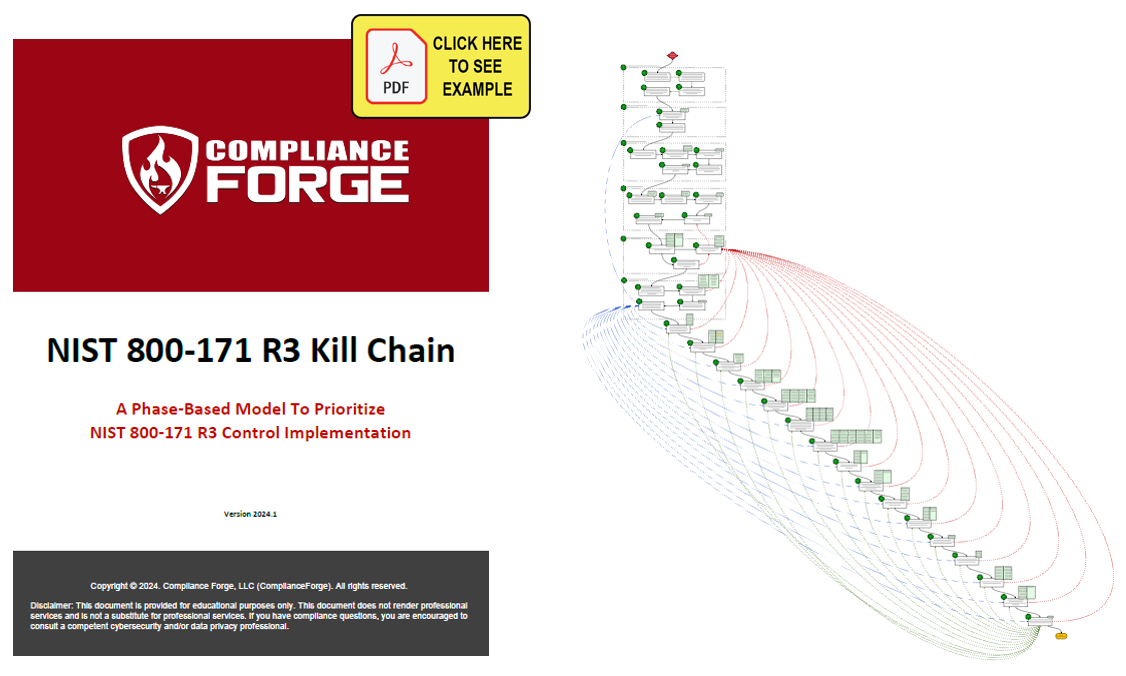
Kill Chain Version - NIST 800-171 R3
The NIST 800-171 R3 version of the Kill Chain is specific to NIST 800-171 R3.
Here is information on the twenty-two (22) phases of the CMMC Kill Chain (these correspond to the picture diagram):
- ESTABLISH CONTEXT FOR CYBERSECURITY & DATA PROTECTION. If you fail to establish context (e.g., facts & assumptions), your entire premise for compliance operations may be incorrect and that could lead you down the wrong path. From a due diligence perspective, establishing context for cybersecurity and data protection should be a holistic endeavor to define all applicable laws, regulations and contractual obligations for cybersecurity and data protection. The reason for this is it is better to have a complete understanding of all requirements at the beginning to avoid reworking in the future, which sacrifices both time and resources. This phase has four (4) sub-components:
- Define the organization's applicable statutory, regulatory and contractual obligations for cybersecurity and data protection (e.g., DFARS, FAR, ITAR, etc.).
- Define what Controlled Unclassified Information (CUI) and/or Federal Contract Information (FCI) is for your specific business case (based on the contract).
- Identify the necessary People, Processes, Technology, Data & Facilities (PPTDF) that are necessary and appropriately sized.
- Develop & implement a resource plan (e.g., business plan, budget, road map, etc.) to meet the organization's unique compliance obligations.
- IMPLEMENT GOVERNANCE PRACTICES. With an understanding of what needs protecting and those associated resources, it is possible to implement appropriate governance practices. This phase has two (2) sub-components:
- Develop, implement and maintain policies and standards to address applicable statutory, regulatory and contractual obligations.
- Prioritize objectives from the resource plan for People, Processes, Technology, Data & Facilities (PPTDF) requirements.
- ESTABLISH THE COMPLIANCE SCOPE. For most organization, there are both internal and external components that are in-scope for NIST 800-171. This phase focuses on eliminating assumptions by clearly documenting where CUI is stored, processed and/or transmitted, as well as developing an inventory of third-parties and their associated roles and responsibilities for protecting FCI/CUI. This phase has five (5) sub-components:
- Create a Data Flow Diagram (DFD) that shows how CUI flows from the DoD all the way down to subcontractors.
- Create and maintain a detailed asset inventory for all systems, applications and services for both in-scope and out-of-scope assets.
- Create a detailed network diagram that includes where CUI is stored, transmitted and/or processed.
- Inventory External Service Providers (ESP) to determine ESP access to CUI and/or in-scope systems, applications and/or services.
- Define roles and responsibilities for internal and external systems, applications and services.
- RISK MANAGEMENT PRACTICES. Risk management is the key building block that other practices rely upon. It is infeasible to govern changes and/or assess vulnerabilities, threats, etc. without first having established risk management practices. Risk management practices establish thresholds for acceptable risk for both internal and external stakeholders. This phase has five (5) sub-components:
- Develop & implement an organization-wide Risk Management Program (RMP) to identify, assess and remediate risk. POA&M deficiencies to prioritize, resource and remediate.
- Document and maintain a Cybersecurity Supply Chain Risk Management (C-SCRM) Plan that is specific to the CUI environment.
- Develop and implement acquisition strategies, contract tools, and procurement methods to operationalize the C-SCRM Plan
- Enforce C-SCRM requirements across the supply chain.
- Establish a process for identifying and addressing weaknesses or deficiencies in the supply chain elements and processes.
- DOCUMENT THE CUI AND/OR FCI ENVIRONMENT. Documenting the CUI and/or FCI environment primarily focuses on populating the System Security Plan (SSP), which should be thought of as a “living document” where the SSP is never complete, since as changes occur throughout the System Develop Lifecycle (SDLC), the SSP also is updated to reflect current technologies, applicable controls and implementation status. This phase has three (3) sub-components:
- Start populating the System Security Plan (SSP). POA&M deficiencies to prioritize, resource and remediate.
- Create and maintain a Plan of Action & Milestone (POA&M) to track and remediate deficiencies.
- Perform a gap assessment from applicable statutory, regulatory and contractual obligations. POA&M deficiencies to prioritize, resource and remediate.
- IDENTIFY COMPLIANCE STAKEHOLDERS. Clearly defined roles and responsibilities are necessary to avoid improper assumptions. For external organizations, this requires contractual obligations to enforce those roles and responsibilities. This has two subcomponent steps:
- Identify compliance stakeholders (including control owners and control operators) and formally assign those individuals roles and responsibilities. From a governance perspective, this can be simplified in a Responsible, Accountable, Supporting, Consulted and Informed (RASCI) matrix.
- Work with Human Resources (HR) to ensure personnel security requirements are integrated into HR operations. POA&M deficiencies to prioritize, resource and remediate.
- Define and implement processes to securely handle CUI wherever CUI is stored, processed and/or transmitted
- Ensure control owners / operators develop, implement and maintain procedures to operationalize the organization's policies & standards.
- POA&M deficiencies to prioritize, resource and remediate.
- DATA PROTECTION PRACTICES. This involves developing and implementing data protection practices to limit logical and physical access to CUI and/or FCI. POA&M deficiencies to prioritize, resource and remediate.
- SEGMENTED NETWORK ARCHITECTURE. This involves implementing a network architecture that ensures it is built on secure engineering principles and enclaves to protect sensitive information (e.g., FCI/CUI). POA&M deficiencies to prioritize, resource and remediate.
- CHANGE MANAGEMENT (CM). This involves developing and implementing Change Management (CM) practices, including a Change Control Board (CCB). POA&M deficiencies to prioritize, resource and remediate.
- INCIDENT RESPONSE (IR). This involves developing and implementing Incident Response (IR) capabilities to detect, respond and recover from incidents (e.g., Incident Response Plan (IRP)). POA&M deficiencies to prioritize, resource and remediate.
- SITUATIONAL AWARENESS (SA). This involves developing and implementing Situational Awareness (SA) capabilities through threat intelligence, log collection and analysis (e.g., SIEM, XDR, etc.). POA&M deficiencies to prioritize, resource and remediate.
- SECURE BASELINE CONFIGURATIONS (SBC). This involves developing and implementing Secure Baseline Configurations (SBC) (e.g., hardening standards) for all technology platforms (e.g., servers, workstations, network gear, applications, databases, etc.). POA&M deficiencies to prioritize, resource and remediate.
- IDENTITY & ACCESS MANAGEMENT (IAM). This involves developing and implementing Identity & Access Management (IAM) capabilities to address "least privilege" and Role-Based Access Control (RBAC). POA&M deficiencies to prioritize, resource and remediate.
- PROACTIVE MAINTENANCE. This involves developing and implementing proactive maintenance practices. POA&M deficiencies to prioritize, resource and remediate.
- ATTACK SURFACE MANAGEMENT (ASM). This involves developing and implementing Attack Surface Management (ASM) practices to identify and remediate vulnerabilities. POA&M deficiencies to prioritize, resource and remediate.
- IT ASSET MANAGEMENT (ITAM). This involves developing and implementing IT Technology Asset Management (ITAM) practices. POA&M deficiencies to prioritize, resource and remediate.
- LAYERED NETWORK DEFENSES. This involves developing and implementing layered network security for Defense-in-Depth (DiD) practices. POA&M deficiencies to prioritize, resource and remediate.
- BUSINESS CONTINUITY & DISASTER RECOVERY (BC/DR). This involves developing and implementing Business Continuity / Disaster Recovery (BC/DR) capabilities. POA&M deficiencies to prioritize, resource and remediate.
- CRYPTOGRAPHIC KEY MANAGEMENT. This involves developing and implementing cryptographic key management and data encryption capabilities. POA&M deficiencies to prioritize, resource and remediate.
- PHYSICAL SECURITY. This involves developing and implementing physical security practices. POA&M deficiencies & document procedures.
- SECURITY AWARENESS TRAINING. This involves developing and implementing training & awareness to ensure a security-minded workforce. POA&M deficiencies & document procedures. POA&M deficiencies to prioritize, resource and remediate.
- INTERNAL AUDIT (IA). This involves developing and implementing an "internal audit" or Information Assurance (IA) capability to govern controls. POA&M deficiencies & document procedures. POA&M deficiencies to prioritize, resource and remediate.